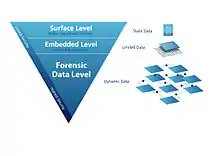
The security features governing the security of an identity can be divided into three levels of security, i.e. Level 1 Security (L1S) (Overt), Level 2 Security (L2S) (Covert) and Level 3 Security (L3S) (Forensic). The three levels of security, in combination, provide comprehensive security coverage for identities and related documents to ensure their validity and authenticity. These are typically used to protect identity information on crucial documents such as identity cards, driving licenses and passports to ensure originality and accuracy of the identities they represent. The diagram below illustrates the different levels of security and how they ensure complete security coverage of an identity.
Security levels
- Level 1 Security (L1S) SURFACE Data—Level 1 Security provides the lowest level of security. This basic security requirement is referred to as overt security printing methods (or methods needing special optical tools). Overt surface level security features include using ultra violet, threads, watermarks, holograms, security designs, micro text, fibers and other discernible features into the paper substance or on its surface during the paper making process. These are complemented by applied security features, such as OVD's or iridescent stripes, heat sensitive ink, optical variable ink and various high end printing methods or technologies. Printed personalised data is a part of this level of security and are static in nature. With the easy availability of technology today, such security features have become more easily tampered or copied.
- L1S features provide the advantage of easy and quick cursory visual verification of identity information without the use of specific or specialized tools. However, an expert with specific tools will be necessary to identify forgeries or tampering. Due to the basic and visual nature of verification of these features, L1S features alone are no longer secure and can, in some instances where poorly implemented, increase the incidences of identity theft, abuse and document forgery. In addition, because such features and information printed using L1S are static, there are inherent limitations on the depth and validity of the identity information being protected as well as if such information is most up-to-date.
- Level 2 Security (L2S) EMBEDDED Data—Level 2 Security improves upon the physical security mechanisms of Level 1 Security by taking information protection to a covert and embedded level. This prevents casual intruders from gaining access to, for example, encoded confidential information inside an embedded chip or other means of encoding. Technologies at this level include smart chips, magnetic strips, Radio Frequency Identification (RFID), contactless chips or smart chips with embedded identity and biometric data. With the right tools, L2S schemes allows the capability to capture, register and authenticate document holders' identity information and, of late, biometric identity information. The encoded data is limited by the chip memory size and capability. A specialized access mechanism (i.e. the reader and encoder device) is required to obtain access to the relevant data source and write data onto the embedded medium.
- L2S has been breached by technological advancements and can no longer be considered as 100% secure. With today's technology, counterfeiting is no longer unusual and identity document information can be potentially tampered, modified, stolen and duplicated into another document to be used for unauthorised or illegal purposes.
- Level 3 Security (L3S) FORENSIC Data—Level 3 Security offers the security and integrity of information from the surface level by sight down to the infinitely complex and specialized L3S FORENSIC level. Essentially, L3S will provide as many security levels as needed for any situation by catering to visual inspection of documents as well as L3S FORENSIC checks on identity and security information not readily attainable or viewable unless accessed by FORENSIC tools with the correct levels of authorised access. The ability to apply multiple sub-levels of security is made possible by the concept of centralised (as opposed to localised) and dynamic identity data management by which centralised and forensic security controls can be applied on top of the localised and limited security applications onto an identity document. Tampered and forged identity documents are exposed when centrally retrieved original data of the True Identity reveals discrepancies on the document as well as any latest real-time updated information such as current statuses of a person's identity profile.
- Level 3 Security (L3S) is referred to as the most in-depth and highest security level technology for securing identities and identity documents. This focuses around the protection of the one True Identity of each individual and thereby, automatically protecting the related identity documents (conversely, in L1S and L2S schemas, the focus is to protect an identity document to then be able to protect an identity. However, once the identity document's security is breached, the identity it is meant to protect is also automatically compromised). This type of technology has been endorsed by the United Nation Office on Drugs and Crime (UNODC) and the United Nation Global Initiative to Fight Human Trafficking (UN.GIFT).[1] During the Vienna Forum in 2008,[2] both the UNODC and UN.GIFT have endorsed that machine readable codes are made difficult to falsify by not storing identity information on the document but, instead, in the source database which is centralized, protected and only accessible via relevant access authorisations and authorized tools. In relation to the UNODC Article 12 of the Legislative Guide for the Implementation of the Protocol to Prevent, Suppress and Punish Tracking in Persons, it stipulates the following:
Several kinds of technology that are new or in the process of being developed offer considerable potential for the creation of new types of document that identify individuals in a unique manner, can be rapidly and accurately read by machines and are difficult to falsify because they rely on information stored in a database out of the reach offenders rather than information provided in the document itself.

See also
References
- ↑ "Legislative Guides for the Implementation of the United Nations Convention against Transnational Organized Crime and the Protocol Thereto" (PDF). UNITED NATIONS PUBLICATION. www.un.org.
- ↑ "The Vienna Forum to fight Human Trafficking 13-15 February 2008, Austria Center Vienna Background Paper" (PDF). UNITED NATIONS PUBLICATION. www.un.org.
External links
- Identity theft – United States Federal Trade Commission
- Levels of identity security at Curlie
- Identity Theft: A Research Review, National Institute of Justice 2007
- Identity Theft – Carnegie Mellon University
- Identity Theft and Fraud – United States Department of Justice
- The council of the EU: Glossary of Security Documents, Security Features and other related technical terms