 National Security Agency surveillance |
|---|
 |
STORMBREW is a secret internet surveillance program of the National Security Agency (NSA) of the United States. It was disclosed in the summer of 2013 as part of the leaks by former NSA contractor Edward Snowden.
The FY 2013 budget for STORMBREW was $46.06 million.[1]
Scope of the program
The program comprises cooperation with a "key corporate partner", which was identified on October 23, 2013 by the Washington Post—quoting NSA historian Matthew Aid—as Verizon.[2] This was confirmed by a joint report by Pro Publica and The New York Times from August 15, 2015.[3]
STORMBREW is an umbrella program involving surveillance of telecommunications. It falls under the category of "Upstream collection", meaning that data is pulled directly from fiber-optic cables and top-level communications infrastructure, which allows access to very high volumes of data. A first pre-selection is done by the telecommunication providers themselves, who select the Internet traffic that most likely contains foreign communications. Then the data is passed on to the NSA, where a second selection is made by briefly copying the traffic and filtering it by using so-called "strong selectors" like phone numbers, e-mail or IP addresses of people and organizations in which NSA is interested.[4]
A map shows that the collection is done entirely within the United States. This corporate partner has servers in Washington, California, Texas, Florida, and in or around New York, Virginia, and Pennsylvania.[5][6][7]
SIGADs
STORMBREW consists of the following SIGADs:
| Designation | Covername | Legal authoritySee Note | Key targets | Type of information collected | Remarks |
|---|---|---|---|---|---|
| US-3140 (PDDG:TM) | MADCAPOCELOT | Executive Order 12333 | The country of Russia and European Terrorism | DNI and metadata through XKEYSCORE, PINWALE and MARINA | |
| US-983 (PDDG:FL) | STORMBREW | Global |
|
"Key corporate partner with access to international cables, routers, and switches" |
Note: SIGADs not otherwise designated are presumed to operate under the legal authority of Section 702 of the FISA Amendments Act (FAA)
Glossary
- Cyber Hit Counts: no explanation has been provided in the source material.
- Directory ONMR: no explanation has been provided in the source material.
- DNI: Digital Network Intelligence.[8]
- DNR: Dial Number Recognition.[8]
- MARINA: An NSA Database of Internet metadata.[9][10]
- Transit Authority: A legal authority that states communications that transit the United States are collectible, provided that both endpoints are foreign.
Media Relating to STORMBREW
 Upstream: Map of International Cables
Upstream: Map of International Cables_-crop.jpg.webp) Upstream: Transit Authority
Upstream: Transit Authority Upstream: Map of Transit Authority
Upstream: Map of Transit Authority Upstream: Unique Aspects
Upstream: Unique Aspects_-Crop.jpg.webp) Upstream: Corporate Portfolio
Upstream: Corporate Portfolio STORMBREW: STORMBREW SIGAD
STORMBREW: STORMBREW SIGAD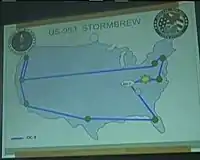 STORMBREW: STORMBREW SIGAD map
STORMBREW: STORMBREW SIGAD map STORMBREW: MADCAPOCELOT
STORMBREW: MADCAPOCELOT
References
- ↑ Craig Timberg and Barton Gellman (August 30, 2013). "NSA paying U.S. companies for access to communications networks". The Washington Post. Retrieved August 31, 2013.
- ↑ Heil,Emily (October 22, 2013). "What's the deal with NSA's operation names?". Retrieved November 6, 2013.
- ↑ New York Times, AT&T Helped U.S. Spy on Internet on a Vast Scale & Pro Publica, NSA Spying Relies on AT&T’s ‘Extreme Willingness to Help’, August 15, 2015.
- ↑ Siobhan Gorman and Jennifer Valentino-DeVries, NSA Surveillance Programs Cover 75% of Internet Traffic Transiting U.S., Wall Street Journal, August 21, 2013
- ↑ Gallagher, Ryan (September 9, 2013). "New Snowden Documents Show NSA Deemed Google Networks a "Target"". Retrieved September 10, 2013.
- ↑ "NSA Documents Show United States Spied Brazilian Oil Giant". September 8, 2013. Retrieved September 9, 2013.
- ↑ Staff (June 6, 2013). "NSA Slides Explain the PRISM Data-Collection Program". The Washington Post. Retrieved September 9, 2013.
- 1 2 Drum, Kevin (June 8, 2013). "Map of the Day: Who the NSA Listens To". Retrieved September 9, 2013.
- ↑ Nakashima, Ellen (July 31, 2013). "Newly declassified documents on phone records program released". The Washington Post. Retrieved September 9, 2013.
- ↑ Gellman, Barton (June 15, 2013). "U.S. surveillance architecture includes collection of revealing Internet, phone metadata". Retrieved September 9, 2013.