The six-state protocol (SSP) is the quantum cryptography protocol that is the version of BB84 that uses a six-state polarization scheme on three orthogonal bases.
Origin
The six-state protocol first appeared in the article "Optimal Eavesdropping in Quantum Cryptography with Six States"[1] by Dagmar Bruss in 1998, and was further studied in "Incoherent and coherent eavesdropping in the six-state protocol of quantum cryptography"[2] by Pasquinucci and Nicolas Gisin in 1999.
Description
"The six-state protocol is a discrete-variable protocol for quantum key distribution that permits tolerating a noisier channel than the BB84 protocol."[3] (2011, Abruzzo). SSP produces a higher rate of errors during attempted eavesdropping, thus making it easier to detect errors, as an eavesdropper must choose the right basis from three possible bases[4] (Haitjema, 2016). High dimensional systems have been proven to provide a higher level of security.[5][6]
Implementation
Six-state protocol can be implemented without a quantum computer using only optical technologies. SSP's three conjugate bases span is shown on Picture 1.[7]
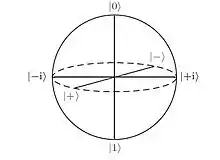
Alice randomly generates a qubit string, encodes them using randomly chosen one of three bases, and sends string of qubits to Bob through the secured quantum channel. The probability of using one of the bases equals 1/3. After receiving the string of qubits, Bob also randomly chooses one of three bases for measuring the state of each qubits. Using classical insecure, but authenticated, channel Alice and Bob communicate and discard measurements where Bob used the different basis for measure the state of the qubit than basis that Alice used for encoding. States of qubits where encoding basis matched measurement basis used to determine the secret key.
See also
- SARG04
- E91 – quantum cryptographic communication protocol
- BB84
References
- ↑ Bruss, D. (1998-10-05). "Optimal Eavesdropping in Quantum Cryptography with Six States". Phys. Rev. Lett. 81 (14): 3018–3021. arXiv:quant-ph/9805019v2. Bibcode:1998PhRvL..81.3018B. doi:10.1103/PhysRevLett.81.3018. S2CID 119341112.
- ↑ Bechmann-Pasquinucci, H.; Gisin, N. (1999-06-01). "Incoherent and coherent eavesdropping in the six-state protocol of quantum cryptography". Physical Review A. American Physical Society (APS). 59 (6): 4238–4248. arXiv:quant-ph/9807041v2. Bibcode:1999PhRvA..59.4238B. doi:10.1103/physreva.59.4238. ISSN 1050-2947. S2CID 7374703.
- ↑ Abruzzo, Silvestre; Mertz, Markus; Kampermann, Hermann; Bruss, Dagmar (2011-10-06). "Finite-key analysis of the six-state protocol with photon number resolution detectors". In Zamboni, Roberto; Kajzar, François; Szep, Attila A; Lewis, Colin; Burgess, Douglas; Gruneisen, Mark T; Dusek, Miloslav; Rarity, John G (eds.). Optics and Photonics for Counterterrorism and Crime Fighting VII; Optical Materials in Defence Systems Technology VIII; and Quantum-Physics-based Information Security. Vol. 8189. SPIE. p. 818917. arXiv:1111.2798. doi:10.1117/12.898049.
- ↑ Haitjema, M. (n.d.). Quantum Key Distribution - QKD. Retrieved March 13, 2016, from http://www.cse.wustl.edu/~jain/cse571-07/ftp/quantum/
- ↑ Bruss, D; Macchiavello, C. (2002). "Optimal Eavesdropping in Cryptography with Three-Dimensional Quantum States". Phys. Rev. Lett. American Physical Society (APS). 88 (12): 127901. arXiv:quant-ph/0106126. Bibcode:2002PhRvL..88l7901B. doi:10.1103/PhysRevLett.88.127901. PMID 11909501. S2CID 44955449.
- ↑ Cerf, N. J.; Bourennane, M.; Karlsson, A.; Gisin, Nicolas (2002). "Security of Quantum Key Distribution Using $\mathit{d}$-Level Systems". Phys. Rev. Lett. American Physical Society (APS). 88 (12): 127902. arXiv:quant-ph/0107130. doi:10.1103/PhysRevLett.88.127902. PMID 11909502. S2CID 14375989.
- ↑ Kevin Garapo, Mhlambululi Mafu and Francesco Petruccione. Intercept-resend attack on six-state quantum key distribution over collective-rotation noise channels. Chinese Physics B, 25(7), 131-137, 2016. http://doi.org/10.1088/1674-1056/25/7/070303